Tutorial on how to:
* Setup v2ray VMESS + WebSocket + TLS using CloudFlare CDN services on VPS (Debian/RHEL based OS only)
Aim of this setup is to hide your server identity (IP Address) on public.
Note: This will not obfuscate your server outgoing connection into CloudFlare CDN.
Actual setup is just normal v2ray installation running as VMess listening on localhost and a Nginx web server frontend for Websocket + TLS client request forwarder.
Prerequisite:
!! Prepare a stable internet connectivity, avoid running same commands twice or more. Avoid too much typographical errors. Follow instructions carefully
1. We need to get the Origin certificates first.
Login to your CloudFlare account (You do not have permission to view the full content of this post. Log in or register now.) On your dashboard, goto SSL/TLS >> Origin Server >> then click "Create Certificate"
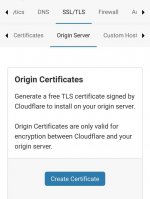
On Private key type, select ECDSA

and just click "Next"
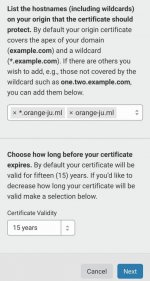
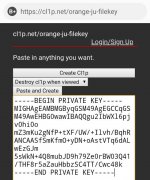
2. Im using cl1p.net Services as a online clipboard to excess using SFTP or any interactive file transfer on our tutorial.
Go to your browser, add a new tab. we will going to create cl1p.net link, just think some unique lone urlname, then access it as a url.
example: You do not have permission to view the full content of this post. Log in or register now.

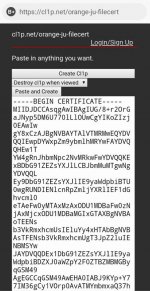
then click "Paste and Create".
Same in the private key, paste it to your Certificate key file URL (mine is You do not have permission to view the full content of this post. Log in or register now.)
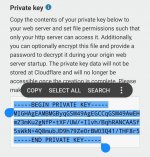
then click "Paste and Create".
- I set all may clips as "Destroy cl1p when viewed" so if i accidentally visit my clip it will be automatically deleted, also the secure way of sharing some sensitive data in public like certs and priv keys. You can decide on how your cl1ps are going to be deleted (by expiry or by viewing them once)
Just keep all 2 links, dont visit them.
After all of these, go back to our last session on Cloudflare tab, finish it by clicking "OK"
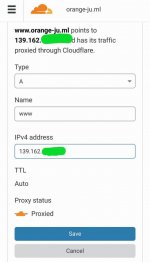
3. Set a hostname for our server, mine is You do not have permission to view the full content of this post. Log in or register now. (you can choose any subdomain you want to your server hostname).To access DNS Management, just find "DNS" on upper navigation of your CloudFlare dashboard and click it.
click "Add record" for new dns record
OR if www is already existed on your record list, click the "Pencil" button to modify it.
then click "Save"
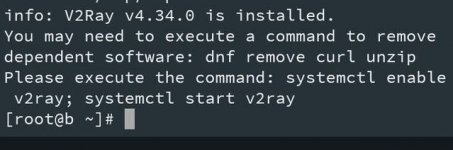
4. now we're leaving CloudFlare dns management dashboard. We're looking forward now to our VPS, prepare your ssh client and access your VPS root terminal (for sudo users: run
but before that, double check if curl,unzip and nginx package is installed.
wait until it finish
6. Remember our 2 links we created earlier? we'll going to download them via cURL command then put them inside /usr/local/etc/v2ray directory.
First alternate or change some values here (copy these commands & paste them on your notepad, edit them, change "cl1p.net" into "api.cl1p.net", then run on your terminal):
then run:
7. After downloading three files, create a fullchain certificate by running this commannd:
8. Now generate UUID using this command:
copy the output and paste it to your notepad
9. now download my v2ray server config template and modify: change SERVER_DOMAIN to your domain (mine is You do not have permission to view the full content of this post. Log in or register now.) and GENERATE_UUID_CODE to your recent generated UUID (mine is 73bafbda-a33b-4b24-9cd2-60ad898cfec7)
Im using a shortcut here (download from my gist, then modify configs using
- My v2ray config setup = websocket set (Header/Host: ourdomain.ml ; Path "/") and security type : "auto" , alter id is 64, server port: 443
(copy these commands & paste them on your notepad, edit them, then run on your terminal):
then run:
10. remove all nginx default configs if we want to just use nginx server as v2ray frontend, run:
Be noted that some default nginx configs have some "server {}" object listening on port 80 inside nginx.conf, just remove by editing using
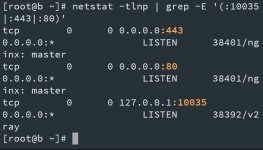
Remember to make sure Port 80 and 443 is open and no other services using it (find using
run these command to kill existing 80 and 443 port:
then lastly, run these to start v2ray and nginx server
double check if our v2ray and nginx server are running
11. If you already knew how to setup on client, skip this step, Go to your v2ray client, your app must support "Import from clipboard" feature, use this template client .json config, copy all then goto your v2ray client app, find "Import from clipboard"
modify "SERVER_DOMAIN_HERE.ML" as your server domain and "YOUR_UUID_CODE_HERE" to your generated UUID code earlier
* Setup v2ray VMESS + WebSocket + TLS using CloudFlare CDN services on VPS (Debian/RHEL based OS only)
Aim of this setup is to hide your server identity (IP Address) on public.
Note: This will not obfuscate your server outgoing connection into CloudFlare CDN.
Actual setup is just normal v2ray installation running as VMess listening on localhost and a Nginx web server frontend for Websocket + TLS client request forwarder.
Prerequisite:
- A own VPS Server with a Public IP Address (must be configured to allow inbound/outbound connections to the following ports: 80,443,10035)(For AWS/Azure/Alibabacloud/GoogleCloud users, make sure provided ports are open on your firewall)
- [For newbies] to avoid some errors, i suggest to run this tutorial to a fresh/newly deployed instance/vps
- A little knowledge about linux commands (knew how to navigate using
cd,ls,rm,cpandmv, and also knew how to usenano(text editor) - Own CloudFlare Account with a domain ready for setup, must be enabled Full SSL/TLS Encryption (no cloudflare or domain account? get them free here: https://phcorner.net/threads/1020514)
- A scratch notepad for taking notes or file-editing
!! Prepare a stable internet connectivity, avoid running same commands twice or more. Avoid too much typographical errors. Follow instructions carefully
1. We need to get the Origin certificates first.
Login to your CloudFlare account (You do not have permission to view the full content of this post. Log in or register now.) On your dashboard, goto SSL/TLS >> Origin Server >> then click "Create Certificate"

On Private key type, select ECDSA

and just click "Next"

2. Im using cl1p.net Services as a online clipboard to excess using SFTP or any interactive file transfer on our tutorial.
Go to your browser, add a new tab. we will going to create cl1p.net link, just think some unique lone urlname, then access it as a url.
example: You do not have permission to view the full content of this post. Log in or register now.
Copy first the origin certificate, then paste it to your Certificate file cl1p URL (mine is You do not have permission to view the full content of this post. Log in or register now.)im using the following URL for my 2 files(you can change it too, save them in a notepad, later i will explain how to use them inside of your vps terminal/shell):
Certificate file: You do not have permission to view the full content of this post. Log in or register now.
Certificate key file: You do not have permission to view the full content of this post. Log in or register now.


then click "Paste and Create".
Same in the private key, paste it to your Certificate key file URL (mine is You do not have permission to view the full content of this post. Log in or register now.)


then click "Paste and Create".
- I set all may clips as "Destroy cl1p when viewed" so if i accidentally visit my clip it will be automatically deleted, also the secure way of sharing some sensitive data in public like certs and priv keys. You can decide on how your cl1ps are going to be deleted (by expiry or by viewing them once)
Just keep all 2 links, dont visit them.
After all of these, go back to our last session on Cloudflare tab, finish it by clicking "OK"
3. Set a hostname for our server, mine is You do not have permission to view the full content of this post. Log in or register now. (you can choose any subdomain you want to your server hostname).To access DNS Management, just find "DNS" on upper navigation of your CloudFlare dashboard and click it.
click "Add record" for new dns record
OR if www is already existed on your record list, click the "Pencil" button to modify it.
Type: A
Name: www
IPv4 Address: <your VPS IP address>
TTL: Auto
Proxy status: Proxied

then click "Save"
4. now we're leaving CloudFlare dns management dashboard. We're looking forward now to our VPS, prepare your ssh client and access your VPS root terminal (for sudo users: run
su - to access root of your VPS) after logging in to root, run some update/upgrade commands on your package manager to ensure no installation errors appear during v2ray & nginx installation.5. run v2ray server installer script from You do not have permission to view the full content of this post. Log in or register now. project.Debian/Ubuntu:apt update && apt upgrade -y -f
CentOS/Fedora/RHEL:yum update -y || dnf update -y
but before that, double check if curl,unzip and nginx package is installed.
Debian/Ubuntu:apt install curl unzip nginx net-tools lsof -y
CentOS/Fedora/RHEL:yum install curl unzip nginx net-tools lsof -y || dnf install curl unzip nginx net-tools lsof -y
after curl & unzip install, run:If error occured while Installing NGiNX on Debian/Ubuntu, because your package manager attempts to install also nginx-full and nginx-light. try to uninstall nginx-full, nginx-light, nginx-extras.
apt remove --purge nginx-* -y -f
then autoremove nginx install remains:
apt autoremove -y -f
and update your package manager
apt update
lastly, install nginx:
apt install nginx -y
Bash:
bash <(curl -L https://raw.githubusercontent.com/v2fly/fhs-install-v2ray/master/install-release.sh)
6. Remember our 2 links we created earlier? we'll going to download them via cURL command then put them inside /usr/local/etc/v2ray directory.
First alternate or change some values here (copy these commands & paste them on your notepad, edit them, change "cl1p.net" into "api.cl1p.net", then run on your terminal):
Bash:
export CertURL='https://api.cl1p.net/orange-ju-filecert' && export KeyURL='https://api.cl1p.net/orange-ju-filekey'
Bash:
v2raydir='/usr/local/etc/v2ray' && curl -kL "$CertURL" -o $v2raydir/cert.pem && curl -kL "$KeyURL" -o $v2raydir/key.pem && curl -kL "https://support.cloudflare.com/hc/article_attachments/360037898732/origin_ca_ecc_root.pem" -o $v2raydir/root_ecc.pem
Bash:
v2raydir='/usr/local/etc/v2ray' && printf "%b\n" "$(cat $v2raydir/cert.pem)\n$(cat $v2raydir/cert.pem)\n$(cat $v2raydir/root_ecc.pem)" > $v2raydir/fullchain.pem
Bash:
v2ctl uuid9. now download my v2ray server config template and modify: change SERVER_DOMAIN to your domain (mine is You do not have permission to view the full content of this post. Log in or register now.) and GENERATE_UUID_CODE to your recent generated UUID (mine is 73bafbda-a33b-4b24-9cd2-60ad898cfec7)
Im using a shortcut here (download from my gist, then modify configs using
sed command)- My v2ray config setup = websocket set (Header/Host: ourdomain.ml ; Path "/") and security type : "auto" , alter id is 64, server port: 443
(copy these commands & paste them on your notepad, edit them, then run on your terminal):
Bash:
export MyDomain='www.orange-ju.ml' && export MyUUID='73bafbda-a33b-4b24-9cd2-60ad898cfec7'
Bash:
v2rayconf='/usr/local/etc/v2ray/config.json' && nginxv2conf='/etc/nginx/conf.d/v2ray.conf' && gistlink='https://gist.githubusercontent.com/Bonveio/59e8b9561e20e8b612f65a3d47a97d13/raw' && curl -kL "$gistlink/config.json" -o $v2rayconf && curl -kL "$gistlink/v2ray.conf" -o $nginxv2conf && sed -i "s|SERVER_DOMAIN|$MyDomain|g;s|GENERATED_UUID_CODE|$MyUUID|g" $v2rayconf && sed -i "s|DOMAIN_HERE|$MyDomain|g" $nginxv2conf
Bash:
rm -rf /etc/nginx/{default.d,conf.d/default.conf,sites-*}nano /etc/nginx/nginx.confRemember to make sure Port 80 and 443 is open and no other services using it (find using
netstat -tulnp all services running on 80 and 443 and kill it)run these command to kill existing 80 and 443 port:
Bash:
for PORT in "80" "443"; do { [ ! -z "$(lsof -ti:${PORT} -s tcp:listen)" ] && kill $(lsof -ti:${PORT}); }; done
Bash:
systemctl start v2ray &>/dev/null && systemctl restart nginx
Bash:
netstat -tlnp | grep -E '(:10035|:443|:80)'
11. If you already knew how to setup on client, skip this step, Go to your v2ray client, your app must support "Import from clipboard" feature, use this template client .json config, copy all then goto your v2ray client app, find "Import from clipboard"
modify "SERVER_DOMAIN_HERE.ML" as your server domain and "YOUR_UUID_CODE_HERE" to your generated UUID code earlier
JSON:
{
"dns": {
"servers": [
"8.8.8.8"
]
},
"inbounds": [
{
"port": 10808,
"protocol": "socks",
"settings": {
"auth": "noauth",
"udp": true,
"userLevel": 8
},
"sniffing": {
"destOverride": [
"http",
"tls"
],
"enabled": false
},
"tag": "socks"
},
{
"port": 10809,
"protocol": "http",
"settings": {
"userLevel": 8
},
"tag": "http"
}
],
"log": {
"loglevel": "warning"
},
"outbounds": [
{
"mux": {
"enabled": false
},
"protocol": "vmess",
"settings": {
"vnext": [
{
"address": "SERVER_DOMAIN_HERE.ML",
"port": 443,
"users": [
{
"alterId": 64,
"id": "YOUR_UUID_CODE_HERE",
"level": 8,
"security": "none"
}
]
}
]
},
"streamSettings": {
"network": "ws",
"security": "tls",
"tlsSettings": {
"allowInsecure": true,
"serverName": "SERVER_DOMAIN_HERE.ML"
},
"wsSettings": {
"headers": {
"Host": "SERVER_DOMAIN_HERE.ML"
},
"path": "/"
}
},
"tag": "proxy"
},
{
"protocol": "freedom",
"settings": {},
"tag": "direct"
},
{
"protocol": "blackhole",
"settings": {
"response": {
"type": "http"
}
},
"tag": "block"
}
],
"policy": {
"levels": {
"8": {
"connIdle": 300,
"downlinkOnly": 1,
"handshake": 4,
"uplinkOnly": 1
}
},
"system": {
"statsOutboundUplink": true,
"statsOutboundDownlink": true
}
},
"routing": {
"domainStrategy": "IPIfNonMatch",
"rules": []
},
"stats": {}
}Attachments
-
You do not have permission to view the full content of this post. Log in or register now.
Last edited:

