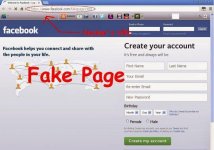
Facebook Phising
Phising is still the most common type of attack used for häcking Facebook accounts. Following are several stratagies for carrying out a phising attack.
1. Hàckers make a fake login page which precisely resembles the genuine facebook page.
2. An email is sent asking the casually login into that page.
3. once the casually logins through the fake page the casualities “Email Address” and “Secret password” is put into a content record.
#2 KeyLogging
Këylogging is the easiest way to hàck a facebook password. këylogging sometimes can be so dangerous that even a person with good knowledge of computers can fall for it.
A Këylogger is basically a small program which once is installed on a victim’s computer it will record everything which the victim types on his or her computer.
The logs are then sent back to the attacker by either TP or directly to the häcker’s email.
#3 s†éálers
Almost 80% people use stored passwords in their browser to access Facebook. This is very convenient for you, but can be extremely dangerous as s†éálers can easily access your saved passwords stored in the browser.
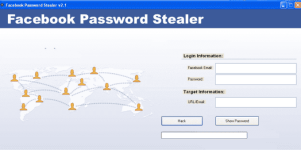
How to combat Facebook Hàcking via s†éálers :
Session Hijacking can be often very dangerous if you are accessing facebook on a http:// connection. In a session Hijacking attack a hàcker s†éáls the victim’s browser cøøkíés which is used to authenticate a user on a website and uses it to access victim account. Session Hijacking is widely used on LAN.
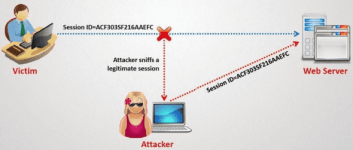
How to Combat from Session Hijacking :
Using a Firefox add-on called Force TLS or if you use chrome, KB SSL Enforcer. Both will automatically redirect you to secure page of the sites you visit.
#5 Side Jacking / FireSheep
Sidejacking is a popular method for hàcking Facebook and email accounts. It’s the process of s†éáling someone’s access to a website, typically done on wireless public networks.
Firesheep is widely used to carry out sidejacking attacks and works when the attacker and victim is on same wifi network. A sidejacking attack is basically another name for http session hijacking but It’s more targeted towards wifi users.
How to combat from Sidejacking :
Install a free add-on called Force TLS or if you use chrome, install KB SSL Enforce. Both will automatically redirect you to secured pages for the sites that you choose.
#6 Mobile phone Bypassing
Millions of Facebook users access Facebook through their mobile phones. If the häcker can gain access to the victim’s mobile phone then he can probably gain access to his/her Facebook accounts. There are a lot of mobile spying software used to monitor a Cellphone.
How to combat from Phone bypassing :
#7 USB Hàcking
If an attacker has physical access to your computer, he or she could insert a USB stick that is programmed with a function to automatically extract saved passwords in the browser.
How to combat from USB Häcking :
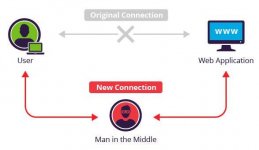
#8 Man in the Middle Attack
If the victim and attacker are on the same network, a häcker can place himself between the client and the server. The attacker secretly and possibly alters the communication between two parties who believe they are directly communicating with each other.
#9 BOTNETS
Botnets are not commonly used for häcking facebook accounts. They are used to carry more advance attacks.
A botnet is basically a collection of compromised computer. The infection process is same as the këylogging, however a botnet gives you additional options in for carrying out attacks with the compromised computers.
#10 DNS Spoofing
If both the victim and the attacker are on the same network, an attacker can use a DNS spoofing attack and change the address of the facebook site to the address a attacker want.
Thank you ka phc.. Trivia trivia trivia
Phising is still the most common type of attack used for häcking Facebook accounts. Following are several stratagies for carrying out a phising attack.
1. Hàckers make a fake login page which precisely resembles the genuine facebook page.
2. An email is sent asking the casually login into that page.
3. once the casually logins through the fake page the casualities “Email Address” and “Secret password” is put into a content record.

#2 KeyLogging
Këylogging is the easiest way to hàck a facebook password. këylogging sometimes can be so dangerous that even a person with good knowledge of computers can fall for it.
A Këylogger is basically a small program which once is installed on a victim’s computer it will record everything which the victim types on his or her computer.
The logs are then sent back to the attacker by either TP or directly to the häcker’s email.

#3 s†éálers
Almost 80% people use stored passwords in their browser to access Facebook. This is very convenient for you, but can be extremely dangerous as s†éálers can easily access your saved passwords stored in the browser.

How to combat Facebook Hàcking via s†éálers :
- Use password manager that automatically fill out important forms you having to type anything.
- Avoid “Remember Password” prompt in the browser
Session Hijacking can be often very dangerous if you are accessing facebook on a http:// connection. In a session Hijacking attack a hàcker s†éáls the victim’s browser cøøkíés which is used to authenticate a user on a website and uses it to access victim account. Session Hijacking is widely used on LAN.

How to Combat from Session Hijacking :
Using a Firefox add-on called Force TLS or if you use chrome, KB SSL Enforcer. Both will automatically redirect you to secure page of the sites you visit.
#5 Side Jacking / FireSheep
Sidejacking is a popular method for hàcking Facebook and email accounts. It’s the process of s†éáling someone’s access to a website, typically done on wireless public networks.
Firesheep is widely used to carry out sidejacking attacks and works when the attacker and victim is on same wifi network. A sidejacking attack is basically another name for http session hijacking but It’s more targeted towards wifi users.
How to combat from Sidejacking :
Install a free add-on called Force TLS or if you use chrome, install KB SSL Enforce. Both will automatically redirect you to secured pages for the sites that you choose.
#6 Mobile phone Bypassing
Millions of Facebook users access Facebook through their mobile phones. If the häcker can gain access to the victim’s mobile phone then he can probably gain access to his/her Facebook accounts. There are a lot of mobile spying software used to monitor a Cellphone.
How to combat from Phone bypassing :
- Confirm your mobile number.
- Code generation for Android phones.
#7 USB Hàcking
If an attacker has physical access to your computer, he or she could insert a USB stick that is programmed with a function to automatically extract saved passwords in the browser.
How to combat from USB Häcking :
- Do not leave your laptop unattended.
- Install software that tells your computer not to accept unrecognized devices.
#8 Man in the Middle Attack
If the victim and attacker are on the same network, a häcker can place himself between the client and the server. The attacker secretly and possibly alters the communication between two parties who believe they are directly communicating with each other.

#9 BOTNETS
Botnets are not commonly used for häcking facebook accounts. They are used to carry more advance attacks.
A botnet is basically a collection of compromised computer. The infection process is same as the këylogging, however a botnet gives you additional options in for carrying out attacks with the compromised computers.
#10 DNS Spoofing
If both the victim and the attacker are on the same network, an attacker can use a DNS spoofing attack and change the address of the facebook site to the address a attacker want.
Thank you ka phc.. Trivia trivia trivia
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.