codebytes4u
Forum Expert
- Joined
- Aug 5, 2016
- Posts
- 1,113
- Reaction
- 28,236
- Points
- 3,684
IPSEC VPN Tunnel on MikroTik Course
Size: 1.66GB
Understand how IPSEC tunneling protocol works and know how to apply it correctly on MikroTik RouterOS.
Understand what is VPN
Understand what is IPSEC
Understand the 4 features of IPSEC
Understand why IPSEC is a protocol suite
Understand the Protocols used in the IPSEC features
Understand IPSEC modes of communications
Understand IPSEC Transport mode
Understand IPSEC Tunnel mode
Understand what is Symmetric key encryption
Understand what is Asymmetric key encryption
Understand how DH works to share the secret key in a secure way
Understand the encryption protocols such as: DES, 3DES, AES, Blowfish, Camellia, RSA & DH
Understand Data Integrity using Hashing algorithms such as: MD5, SHA1, SHA256, SHA512
Understand the types of IPSEC authentication: Pre-shared key vs Certificate
Understand IPSEC Negotiation Protocols: AH vs ESP
Understand the IPSEC negotiation process
Understand what is the initiator to start the IPSEC VPN
Understand IKE Phase 1 (ISAKMP)
Understand the difference between Main and Aggressive mode on IKE Phase 1
Understand IKE Phase 2
Understand what is PFS Group
Understand the difference between IKEv1 & IKEv2
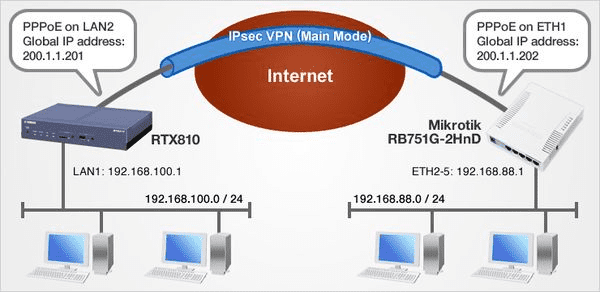
Configuring IPSEC site-to-site using IKEv1
Configuring IPSEC site-to-site using IKEv2
Configure IPSEC IKv2 Remote Access using certificates.
Internet Protocol Security, or what is known as IPSEC, is a VPN protocol suite widely used nowadays in our network to connect 2 or more offices securely to each other using the public internet service, and this will save for companies a lot of cost and time instead of using dedicated leased lines between their offices. However, configuring IPSEC correctly is a challenge because IPSEC is considered as a Framework protocol which has many sub-protocols and phases under its umbrella. I have designed this course to help you to understand how IPSEC works, that means that big part of this course is going to be a theoretical part explaining in details all parts of IPSEC.
Overview
Section 1: Introduction to Virtual Private Network (VPN)
Lecture 1 What is VPN? - Intro
Lecture 2 What is VPN? - Explanation
Section 2: Internet Protocol Security (IPSEC) Framework
Lecture 3 What is IPSEC? - Intro
Lecture 4 What is IPSEC? - Explanation
Lecture 5 IPSEC Protocol suite - Explained
Lecture 6 IPSEC modes of communication - Transport vs Tunnel mode
Lecture 7 Types of Encryption - Symmetric vs Asymmetric
Lecture 8 Security over the internet using IPSEC
Lecture 9 Encyption Protocols (DES - 3DES- AES - Blowfish - Camellia - RSA - DH)
Lecture 10 Data Integrity - Hashing Algorithms (MD5 - SHA1 - SHA256 - SHA512)
Lecture 11 IPSEC Authentication (Pre-shared key vs Certificates)
Lecture 12 IPSEC Negotiation Protocols (AH vs ESP)
Section 3: IPSEC Negotiation Process
Lecture 13 IPSEC Negotiation Process - Introduction
Lecture 14 IPSEC Negotiation Process and choices of IPSEC interesting traffic
Lecture 15 IPSEC IKE Phase 1 (ISAKMP Tunnel)
Lecture 16 IPSEC IKE Phase 1 (Main vs Aggressive mode)
Lecture 17 IPSEC IKE Phase 2 (IPSEC Tunnel)
Lecture 18 IPSEC Data Transfer
Lecture 19 Difference between IKEv1 and IKEv2
Section 4: Site to Site IPSEC VPN
Lecture 20 Introduction to the IPSEC LAB
Lecture 21 Pre-configuration of the IPSEC Tunnel
Lecture 22 Configuring site-to-site IPSEC tunnel using IKEv1 & IKEv2 - Part1
Lecture 23 Configuring site-to-site IPSEC tunnel using IKEv1 & IKEv2 - Part2
Section 5: Remote Access IPSEC IKEv2 VPN
Lecture 24 Introduction to IPSEC IKEv2 Remote Access
Lecture 25 Creating certificates for remote access IPSEC
Lecture 26 Configuring IPSEC IKEv2 remote access
Zip Pass: ELPATRON
Size: 1.66GB
Understand how IPSEC tunneling protocol works and know how to apply it correctly on MikroTik RouterOS.
Understand what is VPN
Understand what is IPSEC
Understand the 4 features of IPSEC
Understand why IPSEC is a protocol suite
Understand the Protocols used in the IPSEC features
Understand IPSEC modes of communications
Understand IPSEC Transport mode
Understand IPSEC Tunnel mode
Understand what is Symmetric key encryption
Understand what is Asymmetric key encryption
Understand how DH works to share the secret key in a secure way
Understand the encryption protocols such as: DES, 3DES, AES, Blowfish, Camellia, RSA & DH
Understand Data Integrity using Hashing algorithms such as: MD5, SHA1, SHA256, SHA512
Understand the types of IPSEC authentication: Pre-shared key vs Certificate
Understand IPSEC Negotiation Protocols: AH vs ESP
Understand the IPSEC negotiation process
Understand what is the initiator to start the IPSEC VPN
Understand IKE Phase 1 (ISAKMP)
Understand the difference between Main and Aggressive mode on IKE Phase 1
Understand IKE Phase 2
Understand what is PFS Group
Understand the difference between IKEv1 & IKEv2
Configuring IPSEC site-to-site using IKEv1
Configuring IPSEC site-to-site using IKEv2
Configure IPSEC IKv2 Remote Access using certificates.
Internet Protocol Security, or what is known as IPSEC, is a VPN protocol suite widely used nowadays in our network to connect 2 or more offices securely to each other using the public internet service, and this will save for companies a lot of cost and time instead of using dedicated leased lines between their offices. However, configuring IPSEC correctly is a challenge because IPSEC is considered as a Framework protocol which has many sub-protocols and phases under its umbrella. I have designed this course to help you to understand how IPSEC works, that means that big part of this course is going to be a theoretical part explaining in details all parts of IPSEC.
Overview
Section 1: Introduction to Virtual Private Network (VPN)
Lecture 1 What is VPN? - Intro
Lecture 2 What is VPN? - Explanation
Section 2: Internet Protocol Security (IPSEC) Framework
Lecture 3 What is IPSEC? - Intro
Lecture 4 What is IPSEC? - Explanation
Lecture 5 IPSEC Protocol suite - Explained
Lecture 6 IPSEC modes of communication - Transport vs Tunnel mode
Lecture 7 Types of Encryption - Symmetric vs Asymmetric
Lecture 8 Security over the internet using IPSEC
Lecture 9 Encyption Protocols (DES - 3DES- AES - Blowfish - Camellia - RSA - DH)
Lecture 10 Data Integrity - Hashing Algorithms (MD5 - SHA1 - SHA256 - SHA512)
Lecture 11 IPSEC Authentication (Pre-shared key vs Certificates)
Lecture 12 IPSEC Negotiation Protocols (AH vs ESP)
Section 3: IPSEC Negotiation Process
Lecture 13 IPSEC Negotiation Process - Introduction
Lecture 14 IPSEC Negotiation Process and choices of IPSEC interesting traffic
Lecture 15 IPSEC IKE Phase 1 (ISAKMP Tunnel)
Lecture 16 IPSEC IKE Phase 1 (Main vs Aggressive mode)
Lecture 17 IPSEC IKE Phase 2 (IPSEC Tunnel)
Lecture 18 IPSEC Data Transfer
Lecture 19 Difference between IKEv1 and IKEv2
Section 4: Site to Site IPSEC VPN
Lecture 20 Introduction to the IPSEC LAB
Lecture 21 Pre-configuration of the IPSEC Tunnel
Lecture 22 Configuring site-to-site IPSEC tunnel using IKEv1 & IKEv2 - Part1
Lecture 23 Configuring site-to-site IPSEC tunnel using IKEv1 & IKEv2 - Part2
Section 5: Remote Access IPSEC IKEv2 VPN
Lecture 24 Introduction to IPSEC IKEv2 Remote Access
Lecture 25 Creating certificates for remote access IPSEC
Lecture 26 Configuring IPSEC IKEv2 remote access
You do not have permission to view the full content of this post. Log in or register now.
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.