PHC-PROXYPIRATE
Forum Contributor
- Joined
- Jun 17, 2020
- Posts
- 12,726
- Solutions
- 3
- Reaction
- 63,147
- Points
- 8,872
ALLNETWORKS NO LOAD NO PROMO BUG IP'S BOGONS REVEAL NA
 Gtm
Gtm
 Sts
Sts
 Gomo/Ghpw
Gomo/Ghpw
 Dito
Dito
 All Telco
All Telco
 No Load No
No Load No 
 No Cap No Block All
No Cap No Block All
3 Bogons BugIP's Lang Muna Mga Lods Hehe .
.
Choose Wisely .
.
Sorry Po Mga Lods Kung Medyo Natagalan .
.
Kumain Po Muna Kasi Ako Eh .
.
Note: Hindi Sya Alive Sa Host Checker Ng HTTP Injector Piro Working Naman Sya Mga Lods .Kasi Nga Bogons
.Kasi Nga Bogons  .
.
3 Bogon/s IP's Address Here . [Open For All Just React To See
. [Open For All Just React To See  ] % [No Minimum & Maximum Post Counts
] % [No Minimum & Maximum Post Counts  ]
]
Lakas Basta Bogons

 ...
...
So What Is A Bogon/s?
Here . [Complete Definition] & [Open For All]
. [Complete Definition] & [Open For All]
“Bogon” is an informal term used to describe IP packets on the public Internet that claim to be from an area of the IP address space reserved, but not yet allocated or delegated by the Internet Assigned Numbers Authority (IANA) or any of the Regional Internet Registries (RIR). Private IP addresses are also considered bogons because they are not supposed to be found on the public Internet. Many ISPs and end-user firewalls seek to block bogons, because they have no legitimate use (more details on how successful they can be at this are below). The only reason you will see a bogon is if someone either accidentally misconfigured something or intentionally is creating them for malicious purposes.
Bogon packets are useful to cybercriminals because the packets cannot be attributed to an actual host (since the source IP is bogus). Routers don’t examine the source IP address of a packet, all they care about is the destination IP address, so routers will happily forward bogon packets to their destination.
A bogon packet cannot be used to initiate and set up a TCP connection (setting up a TCP connection requires a 3-way handshake between two endpoints). So bogon packets cannot be used to, for example, send spam e-mails or to send HTTP/web traffic. But bogon’s can be used to launch TCP SYN attacks and are used in about 10% of DDoS attacks on the net. Stopping bogons can not only help your enterprise but those you connect to. Bogons can also be used to covertly move information.
Enterprises have been filtering bogons for years. Some did it better than others. Those that did it well could reduce the amount of malicious traffic heading their way. Historically, when ISPs or enterprises say they filter bogons, they are likely only referring to private IP addresses, not the full bogon address space. Filtering private IP addresses requires only a few rules. But filtering the full bogon list requires about 5000 rules for IPv4 and about 70,000 rules for IPv6. Double those numbers numbers if you want to filter in both directions. Given that 5000 rules will cause performance degradation in firewalls and router ACLs, it is likely that few, if any, ISPs and enterprises are filtering the full bogon list.
Some other very important notes for context:
• Bogon addresses are not static. Addresses get assigned and unassigned and changed. So while the core of a bogon list may remain the same for long periods of time the list is dynamic enough to need to be frequently updated if you want to use it to block. Automated systems like the Centripetal Networks RuleGate can take dynamic feeds of bogons and block them, automatically.
• It is worth mentioning that there is only one device on the market capable of processing enough rules to block bogons, including in both directions, and that is the RuleGate.
• Additionally, IPv4 networks are not safe from an IPv6 bogon bandwidth flooding attack. Most ISPs and many enterprises use dual-mode equipment which can route both IPv4 and IPv6 and have IPv6 routing tables in place and have pre-allocated IPv6 to their subscriber’s networks.
• The dual-mode, IPv6 capable systems in your network can also enable malicious actors to do other things, like exfil their data using IPv6 without you knowing it. Although this is not the precise definition of a bogon, this unauthorized use of your network is bogus and bad and should also be stopped.
• I hope this discussion on bogons has got you thinking. Part of the reason there has not been much discussion of bogons is till now there were no automated systems that could really stop them. Now there is and it is worth having the conversation.
• By the way, an absolutely great reference to this topic is “The Bogon Reference” by Team Cymru, a community focused team of cyber defenders who are great at tracking the complexities of these issues, including updated bogon lists.
Note: The Completely Definition Is Credits To Google .
.
Edit: AS4775 announces bogons
You do not have permission to view the full content of this post. Log in or register now.
 Philippines
Philippines 
Edit: Ito Gawin Nyu Sa Mga Dipa Alam Kung Paano Mag Set Up .
.
How To Set Up? [Open For All]
[Open For All]
1st
Create Account In Fastssh Or Any V2Ray/Vless Site That You Know.
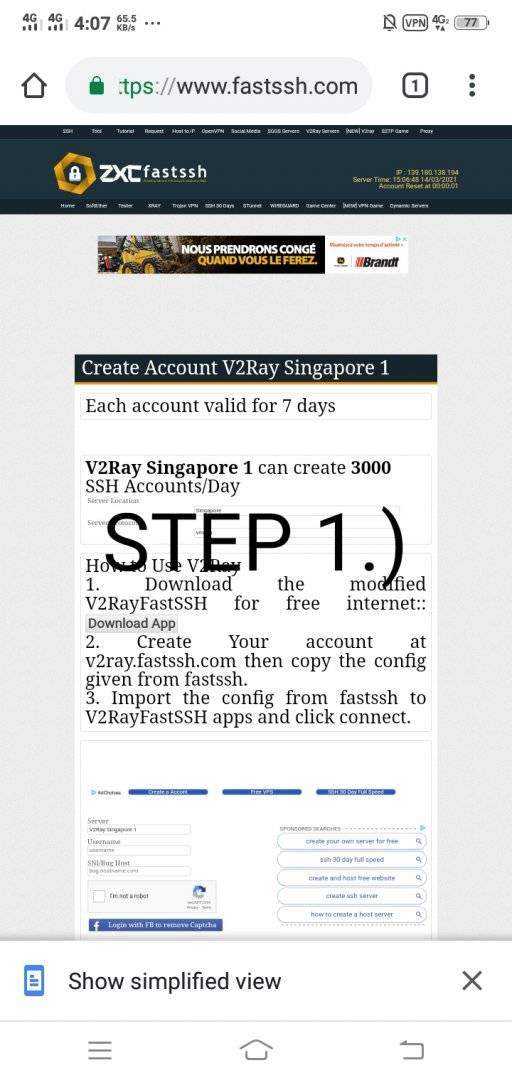
2nd
Copy The V2Ray/Vless Account And Paste In In Your Notes.
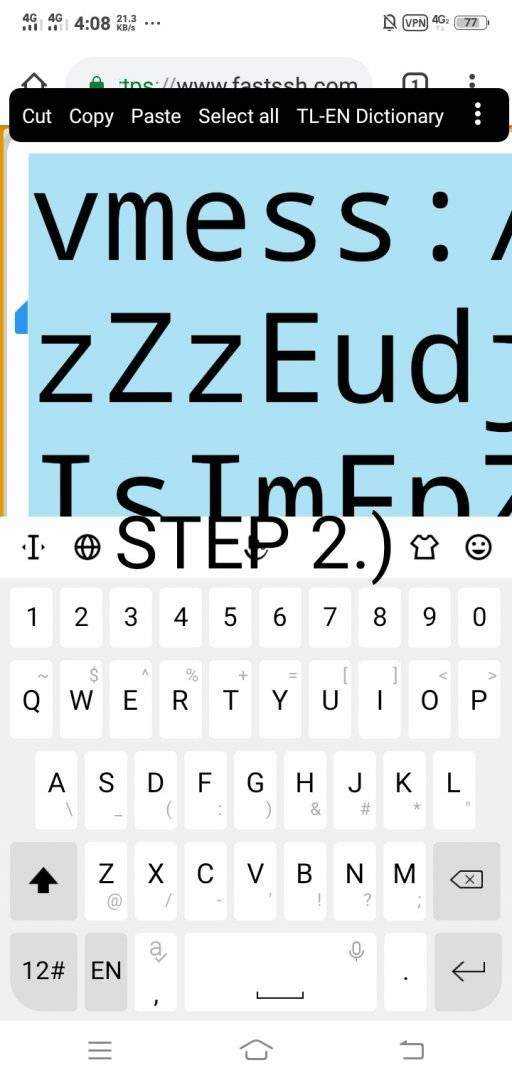
3rd
For HTTP Injector & NapsterNetV Open In Menu Click V2Ray Settings And Click On + Sign And Paste The V2Ray/Vless Account That You Created.
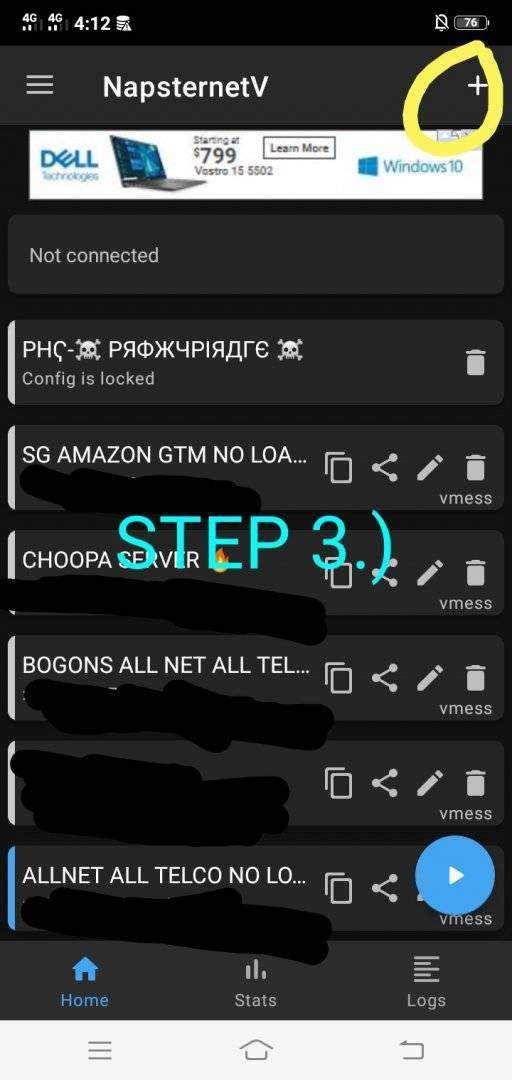
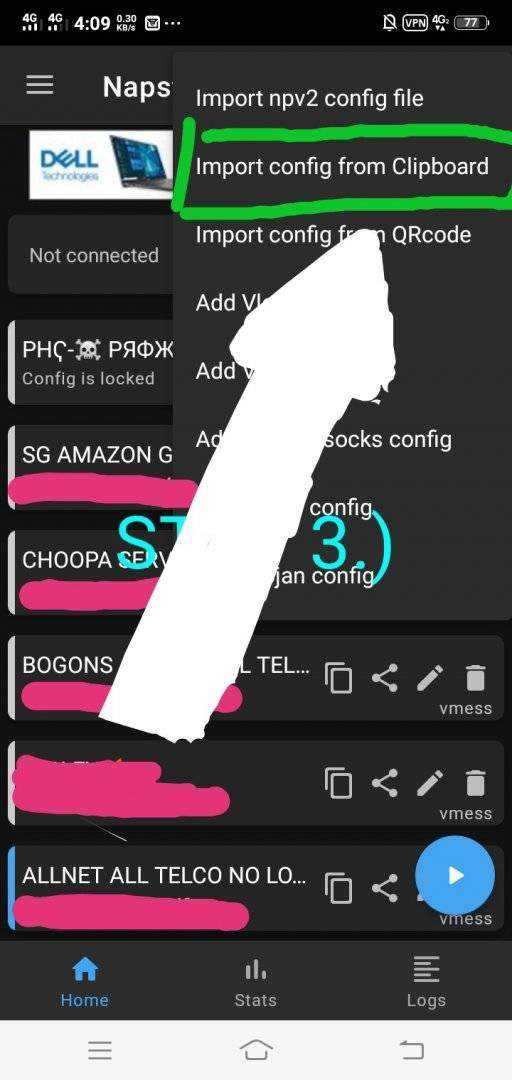
4th
The Final Set Up Enable The Mux And Set To 8 Only.
Note: Tls To Sni or Sni is to Tls.
Means Vice Versa Kabaligtaran In Tagalog And Done Happy Browsing .
.
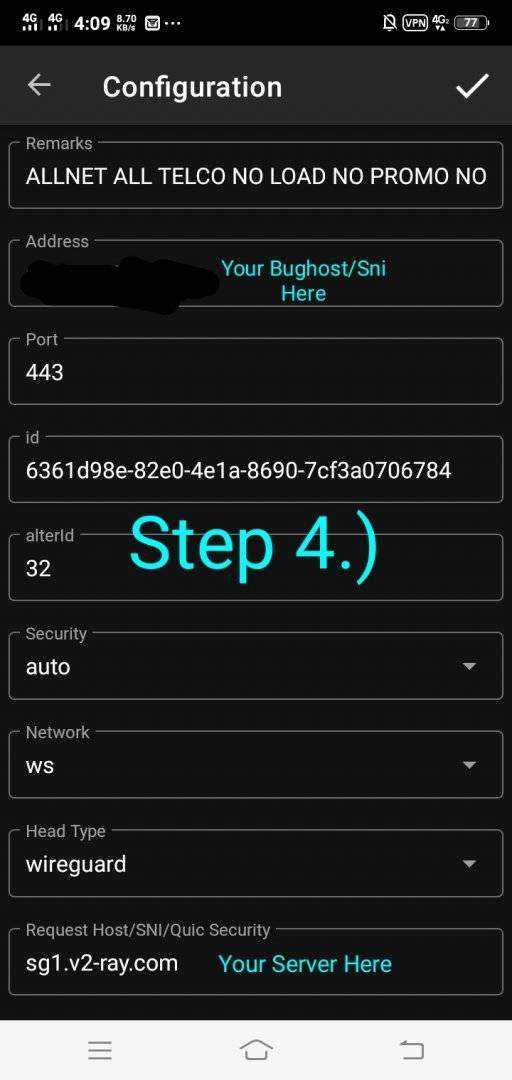
 Gtm
Gtm
 Sts
Sts
 Gomo/Ghpw
Gomo/Ghpw
 Dito
Dito
 All Telco
All Telco
 No Load No
No Load No 
 No Cap No Block All
No Cap No Block All
3 Bogons BugIP's Lang Muna Mga Lods Hehe
 .
.Choose Wisely
 .
.Sorry Po Mga Lods Kung Medyo Natagalan
 .
.Kumain Po Muna Kasi Ako Eh
 .
.Note: Hindi Sya Alive Sa Host Checker Ng HTTP Injector Piro Working Naman Sya Mga Lods
 .Kasi Nga Bogons
.Kasi Nga Bogons  .
.3 Bogon/s IP's Address Here
 . [Open For All Just React To See
. [Open For All Just React To See  ] % [No Minimum & Maximum Post Counts
] % [No Minimum & Maximum Post Counts  ]
]
You do not have permission to view the full content of this post. Log in or register now.
Lakas Basta Bogons


 ...
...So What Is A Bogon/s?

Here
 . [Complete Definition] & [Open For All]
. [Complete Definition] & [Open For All]“Bogon” is an informal term used to describe IP packets on the public Internet that claim to be from an area of the IP address space reserved, but not yet allocated or delegated by the Internet Assigned Numbers Authority (IANA) or any of the Regional Internet Registries (RIR). Private IP addresses are also considered bogons because they are not supposed to be found on the public Internet. Many ISPs and end-user firewalls seek to block bogons, because they have no legitimate use (more details on how successful they can be at this are below). The only reason you will see a bogon is if someone either accidentally misconfigured something or intentionally is creating them for malicious purposes.
Bogon packets are useful to cybercriminals because the packets cannot be attributed to an actual host (since the source IP is bogus). Routers don’t examine the source IP address of a packet, all they care about is the destination IP address, so routers will happily forward bogon packets to their destination.
A bogon packet cannot be used to initiate and set up a TCP connection (setting up a TCP connection requires a 3-way handshake between two endpoints). So bogon packets cannot be used to, for example, send spam e-mails or to send HTTP/web traffic. But bogon’s can be used to launch TCP SYN attacks and are used in about 10% of DDoS attacks on the net. Stopping bogons can not only help your enterprise but those you connect to. Bogons can also be used to covertly move information.
Enterprises have been filtering bogons for years. Some did it better than others. Those that did it well could reduce the amount of malicious traffic heading their way. Historically, when ISPs or enterprises say they filter bogons, they are likely only referring to private IP addresses, not the full bogon address space. Filtering private IP addresses requires only a few rules. But filtering the full bogon list requires about 5000 rules for IPv4 and about 70,000 rules for IPv6. Double those numbers numbers if you want to filter in both directions. Given that 5000 rules will cause performance degradation in firewalls and router ACLs, it is likely that few, if any, ISPs and enterprises are filtering the full bogon list.
Some other very important notes for context:
• Bogon addresses are not static. Addresses get assigned and unassigned and changed. So while the core of a bogon list may remain the same for long periods of time the list is dynamic enough to need to be frequently updated if you want to use it to block. Automated systems like the Centripetal Networks RuleGate can take dynamic feeds of bogons and block them, automatically.
• It is worth mentioning that there is only one device on the market capable of processing enough rules to block bogons, including in both directions, and that is the RuleGate.
• Additionally, IPv4 networks are not safe from an IPv6 bogon bandwidth flooding attack. Most ISPs and many enterprises use dual-mode equipment which can route both IPv4 and IPv6 and have IPv6 routing tables in place and have pre-allocated IPv6 to their subscriber’s networks.
• The dual-mode, IPv6 capable systems in your network can also enable malicious actors to do other things, like exfil their data using IPv6 without you knowing it. Although this is not the precise definition of a bogon, this unauthorized use of your network is bogus and bad and should also be stopped.
• I hope this discussion on bogons has got you thinking. Part of the reason there has not been much discussion of bogons is till now there were no automated systems that could really stop them. Now there is and it is worth having the conversation.
• By the way, an absolutely great reference to this topic is “The Bogon Reference” by Team Cymru, a community focused team of cyber defenders who are great at tracking the complexities of these issues, including updated bogon lists.
Note: The Completely Definition Is Credits To Google
 .
.Edit: AS4775 announces bogons
You do not have permission to view the full content of this post. Log in or register now.
 Philippines
Philippines 
Edit: Ito Gawin Nyu Sa Mga Dipa Alam Kung Paano Mag Set Up
 .
.How To Set Up?
 [Open For All]
[Open For All]1st
Create Account In Fastssh Or Any V2Ray/Vless Site That You Know.
2nd
Copy The V2Ray/Vless Account And Paste In In Your Notes.
3rd
For HTTP Injector & NapsterNetV Open In Menu Click V2Ray Settings And Click On + Sign And Paste The V2Ray/Vless Account That You Created.
4th
The Final Set Up Enable The Mux And Set To 8 Only.
Note: Tls To Sni or Sni is to Tls.
Means Vice Versa Kabaligtaran In Tagalog And Done Happy Browsing
 .
.Attachments
-
You do not have permission to view the full content of this post. Log in or register now.
Last edited:





