Strawberrry
Forum Veteran
- Joined
- Aug 2, 2016
- Posts
- 1,598
- Solutions
- 4
- Reaction
- 633
- Points
- 524

doxing
Doxing is a technique of tracing someone or gather information about an individual using sources on the internet. Its name is derived from “Documents” or “Docx”. Doxing method is based purely on the ability of the häçker to recognize valuable information about his target and use this information to his benefit. It is also based around the idea that, “The more you know about your target, the easier it will be to find his or her flaws”
Contents
- Post 1
- Introduction
- Contents
- Doxing
- Post 2
- De-tracing
- Post 3
- Anonymity
- Post 4
- Resources Links
- Post 5
- Credits

How can a dox process look like?
Take the scenario where you are selling a product and someone makes a chargeback. What do you have to begin with?
(In this scenario the payment was made with Bitcoin)
- IP Address
- First of all you can locate the IP address
- Then you can start looking up the IP on databases
- From that you will get new data (IP addresses, Emails, passwords)
- And you continue looking the new data up and connecting it.
- Then you are able to find social medias with the helps of the emails.
- And you continue building on..
That is how a dox can look like, of course it is different for all occasions. But this is how it looked like for me recently. The point is that you should always keep building and confirming the information that you have. If you know its geo-location that is in France and then you have a Facebook account where he's clearly not from France, then you can maybe rule it out and keep or digging.
What can I do with a dox?
There are many things that I could mention, but they are mostly black hat related things which are disallowed to discuss. But take the scenario that I mentioned above, you get scammed online, they should be expected to be doxed then; you can use the dox to get back what you lost. You are honestly only limited by your imagination. This is what you can theoretically do:
- You can leak the dox for other people to use the information provided. The most common way to leak is through Pastebin and such. Here are the most common ones:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
- If you have your target's IP address and you go to IP-tracker sites and then basically send an abuse notice to his hosting provider. Here are some commonly used IP-tracker sites:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
- There are so much more. But as I mentioned, it is mostly black hat related things. But if you actually talking about a real fraud here, or you know that this person has committed any crimes, you can use the dox to report that person to the FBI or your local police.
When doxing, you will be using many different websites to gather information about your target. Using your web browser's bookmark field, you can create a folder within folders and so on; create a new folder and name it "Doxing" and inside you can have sub-folder for different resources when doxing. For example "Dox release", "IP tools", "Using the real name", "Using phone number" and such, collect your resources within the folders to have it easily accessible.
Resources folder
So when doxing, you most likely want a doxing template to parse information you gather. Use a template and save it in a text editor to edit throughout your process of doxing. There are tons templates online; all are pretty much the same, they all look something like this:
Code:
[#] [Personal Information]
Full Name:
Date of Birth:
Phone Number:
Email:
Skype(s):
Facebook:
Twitter:
YøùTùbé:
Other:
[#] [Additional]
Pictures:
Other:
IP Address:
Hobbies:
Alias(es):
[#] [Living]
Address:
Landline:
City:
State:
ZIP:
Country:
Occupants:
Flat/House:
Bedrooms:
[#] [Optional]
Family member:
Date of birth:
Job:
Facebook:
Picture:
Other:
[#] Reason of Dox:Using Skype
Deals and such are often dealt over Skype because of its massive communication platform, and things can easily go wrong over there; a currency exchange scam, your partner might try to play you, threats against you or your family, and much more. Knowing how to use your targets Skype in order to dox is crucial to know. Sometimes the best place to start is the least obvious. (If you have your target on Skype) Click on your target's avatar; you will get information such as birth date, gender, language, skype name, phone number, and country.
Birth date: While this is not always correct, considering that most people put fake birth dates, this can potentially be used to compare to another birth date that you parse from another investigation method.
Gender: This is in most cases true, you do not have much use of this information thought.
Language: Many people do not put their native language there. Instead, they put English, but in some cases, you will find people having their language set as their native.
Skype name: This is, of course, the most important, will show you below how to use this to parse more information.
Phone number: Believe it or not, but there are people who accidentally set their actual phone number here because they are not aware that it is public.
Country: Not important, it depends on how the language situation is looking.
You mainly want to use that information to compare, not to use for your actual dox and that is because of how unreliable it is; most of the times, the information is fake. - So, moving on to using your victims Skype name; to just Google, the Skype name directly won’t get you as far as this command will get you:
Code:
skype: usernameSo, “what can I do with this search” is something you might be wondering, and first of all, if this user is registered here on häçk Forums, and the user have ever made a post saying something like “Hey, add my Skype ******”, then you will be able to find that post with this search, and there you go, you now have his häçk Forums account. You can add that to “Other” in the doxxing template. Continuing using only the Skype ID. So there are something named “Skype resolver”, basically it gets the IP-address of your target. Skype resolvers comes and goes, but there are ones that are working as of (03/00/2017) which are:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
With the two mentioned above, the user needs to be Online. And there is You do not have permission to view the full content of this post. Log in or register now.one which can be used to see if the IP has been stored using the resolver before.
Email to Skype
There are two methods to go from Email to Skype and the first one is using sites such as:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
The second one is the best and easiest which is when you simply go to the search field of Skype and enter the email. Then you will get Skype(s) which as the email connected to it.
IP to Skype
Same goes here, these two sites provides this type of search:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
Skype to Email[/list]
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
Locating your target
The IP-addresses that you gathered from the Skype resolver might not be your target’s current ones, but they might show the correct location. First of all, you can add the IP-address to the template, and secondly, you can use the IP-address to get the location of him. Head over to; You do not have permission to view the full content of this post. Log in or register now. - enter one IP address a time that you got from “Database records” on your Skype resolver site. Compare every search and then decide which one is probably the one. You will be getting information beyond your imagination! Such as ISP provider, Country, Capital, State, City Location, Postal, Hostname, and much more. Head over to your doxing template, add new tabs and fill in old.
Finding your target’s email address
There are some methods that I would want to show, but they are not allowed to be discussed here on the forum. They are mostly based on using your target’s Paypal, Amazon and eBay in order to get their information, but I won’t go any further from here. Facebook can be a very useful site when it comes to acquiring information, especially someone's email address. Make a simple Google search of your target’s real name and see if you can find his or hers Facebook. If they have their details open for everyone, just grab their email from there. When it comes to Facebook, you can also import your contacts through Yahoo to find their email. So go ahead and create a Yahoo account and on the top left corner where it says “contacts”, simply choose Facebook. Login and import the contacts and then you should have their email.
Other than that you can use Skype to your advantage. There are two Skype2Email services that I tend to use:
- You do not have permission to view the full content of this post.
Log in or register now.
- You do not have permission to view the full content of this post. Log in or register now.
Tip: Sometime’s the most obvious place to look is the last place you look. Did your target ever send you any money over Paypal or such site? Check the transaction details for their email.
Using your target’s email address
Having your target’s email address is definitely one of the better things to have considering that every service online is connected to an email, and some of them display it public for different reasons. There are a few common methods that you can use:
- Email to Skype method
[1] So, there are two methods to find your target’s Skype using Email. The first one, is very basic, just like the mentioned Facebook method above. Head over to Skype and in the “Search” field, enter the email and hit “Search Skype”. Simple as that, if you target has a Skype connected with the email you entered, you will find it.
[2] The second method to do this is to again use the You do not have permission to view the full content of this post. Log in or register now. site. Head over to the “You do not have permission to view the full content of this post. Log in or register now.” tab and simply enter the email you wish to look up.
Search result
- The PayPal method
Again, very basic yet very effective. Just be careful, this method will include you having to send money, which will tell your information as well. Make sure that you are hidden and safe. So, you have your target’s email, simply make a new transaction and send the minimum amount possible ($0.01), when sent, head over to the main page and click on the transaction. Make sure that you send as “Friends and family”.
You will get your target’s first name and last name using this method.
Getting house information
Using You do not have permission to view the full content of this post. Log in or register now. and You do not have permission to view the full content of this post. Log in or register now. you can get information such as; how many baths they have; when the house was built, how big their yard is, how much their house is worth and such. You can also use You do not have permission to view the full content of this post. Log in or register now. to get a better view where they live. This is something again that you can add to your doxxing template, take screenshots and add data.
Zillow data

Sift Tool
Dumps / Combo Lists
Providing accounts that don't belong to you, whether in trades, for sale, or free, dumps are not allowed. The definition of a
dump is a file with logins, passwords, personal details or emails. We do define "combo lists" as dumps as well.
First, create a map on your desktop and name “Databases” or whatever you deem fit. Head over to You do not have permission to view the full content of this post. Log in or register now. and download a version that works for your operating system. Then you simply copy Sift.exe and the license file to the folder you created, then add your databases in there. It uses the command prompt to work. So when you want to search in your databases you need to know some basics of Command Prompt. You created your folder on your desktop, and if you named it “Databases”,
this should be your directory “C:\Users\Maxim\Desktop\Databases” except for “Maxim” which is my computer name. If you are unsure what your folder directory is named, simply locate it in file explorer and copy the URL.
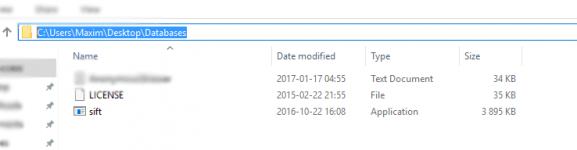
Copy the URL and head over to Command Prompt. Type “CMD” in your start menu and run as administrator. Once in CMD, you need to change your directory. You do that by typing “cd C:\Users\Maxim\Desktop\Databases”.
Now to use Sift-tool you enter a new command:
Code:
sift häçker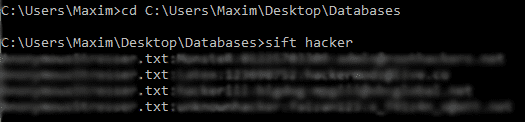
Colored logs
Now, what would be cool to have? You guessed it right, colors. Head over to You do not have permission to view the full content of this post. Log in or register now. and click the “ANSICON v1.66” or whatever version is the latest. Download it and extract it to a folder on your desktop. Head back to your Command Prompt and change your directory to the Ansicon folder on your desktop. Make sure it sets to either x64 or x86 depending on what you have. You can use the same method as we did before. Open up file explorer and copy the URL. Mine in this case is:
Code:
C:\Users\Maxim\Desktop\Ansicon\x64
Code:
ansicon.exe -i
Code:
sift -ria --color --err-skip-line-length --stats --write-config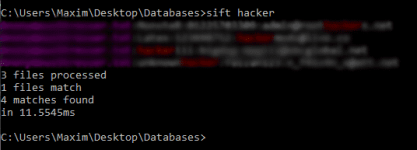
Using name and aliases
Obviously having the name can be very useful if you know how to proceed correctly with it. There are different sites for each country, I have provided lists on the penultimate post. If you are looking to search using the name from a particular country, try to Google and see if you can find one, otherwise, just private message me and I will see if I have one. With the help of their name, you can get information such as relatives, address, phone number, zip code and so on. Here are name searching sites for a few countries:
- You do not have permission to view the full content of this post.
Log in or register now. (US and more)
- You do not have permission to view the full content of this post.
Log in or register now. (Canada)
- You do not have permission to view the full content of this post.
Log in or register now. (UK)
- You do not have permission to view the full content of this post.
Log in or register now. (Sweden)
- You do not have permission to view the full content of this post.
Log in or register now. (Denmark)
- You do not have permission to view the full content of this post. Log in or register now. (Germany)
Finding Social Media Accounts
Finding social medias accounts might not always be the most obvious thing. Your first thoughts might be to simply search their name in the search field of etcetera Facebook or Twitter, but you may get too many results to be able to find which is the one you are looking for. So it is better to go by their email as it can only give a correct result. You can use the following:
- You do not have permission to view the full content of this post.
Log in or register now. allows you to search by using their email, name, username or phone and optional by using their location. This one is my personal favorite for when it comes to finding Google Plus and Facebook accounts.
- You do not have permission to view the full content of this post.
Log in or register now. only allows you to search using their username but it can still be very useful because it has more sites and because it is very easy to locate around to quickly find what you are looking for.
- You do not have permission to view the full content of this post.
Log in or register now. only allows you to search by using either email or real name. It basically provides links that will do the searching for you, personally, I do not find this site very efficient.
- You do not have permission to view the full content of this post.
Log in or register now. is another user friendly site but still not the top choice as its results are always too few when there's more to find. You can search by using their real name and optional by adding street, city, state or Zip code.
- You do not have permission to view the full content of this post. Log in or register now. is an absolute go-to site if your search is within the United States as it displays searches well. Search by using their real name and state and you will get the result of each person and their email(s). You can also reverse search for an e-mail address.
Using phone number
If you know where to search for who, you are able to get name, address, state and such from just a phone number. Just like we did with names above, you need a specific site for each country, you can use You do not have permission to view the full content of this post. Log in or register now.for US search,You do not have permission to view the full content of this post. Log in or register now.for Canada search, You do not have permission to view the full content of this post. Log in or register now.for German people. If you need to find for a specific country, simply Google for etcetera "Brazil phone number search".
Zip Code Doxing
A Zip code can give you a general location, it might not be the most useful doxing part ever, but if you have multiple data about something, you can rule out some of them with the help of the location. For US searches you can use You do not have permission to view the full content of this post. Log in or register now. where you simply enter the Zip Code that you want to look up and it will return your city, state, county, area code, timezone and such. As I said, it is not the most useful thing ever, but on some occasions, it will serve you well.
Using images
So using images when doxing is just like searching the web, but instead of searching with a text you are searching with images. If your target is using the same image on an online forum as on Facebook you should be able to find his or hers other accounts. You can use You do not have permission to view the full content of this post. Log in or register now. or You do not have permission to view the full content of this post. Log in or register now. for searching with images to find connections or to use text to find images. In our case, we will most likely want to search with images for connections to other images in hope of finding the same image on another site. Simply drag and drop the image and look at the result. You can of course also right-click an image and click "Google Search This Image" which should give you the same result as You do not have permission to view the full content of this post. Log in or register now.. You can also use EXIF data which is explained on You do not have permission to view the full content of this post. Log in or register now.:
EXIF is short for Exchangeable Image File, a format that is a standard for storing interchange information in digital photography image files using JPEG compression. Almost all new digital cameras use the EXIF annotation, storing information on the image such as shutter speed, exposure compensation, F number, what metering system was used, if a flash was used, ISO number, date and time the image was taken, white balance, auxiliary lenses that were used and resolution. Some images may even store GPS information so you can easily see where the images were taken!
EXIFdata.com is an online application that lets you take a deeper look at your favorite images!
Using a website
If your target has a website and has not protected it well or used any fake information when signing up, chances are that you will be walking away with a lot of information. You can use a site such as You do not have permission to view the full content of this post. Log in or register now. or You do not have permission to view the full content of this post. Log in or register now. where you simply enter the domain you would like to look-up and you get the information of it if it is not private. I used Facebook's domain for this tutorial, and this is what i got:
Registry Registrant ID:
Registrant Name: Domain Administrator
Registrant Organization: Facebook, Inc.
Registrant Street: 1601 Willow Road,
Registrant City: Menlo Park
Registrant State/Province: CA
Registrant Postal Code: 94025
Registrant Country: US
Registrant Phone: +1.6505434800
Registrant Phone Ext:
Registrant Fax: +1.6505434800
Registrant Fax Ext:
Registrant Email:
...
More
Steam Doxing
Steam doxing isn't the easiest but it is possible. First of all, you can check for links on their profile page. But the main thing when doxing on Steam is about looking for records if they have ever been banned from a gaming community or such. If they are playing Counter-Strike for example and have ever been banned, you should be able to find it by searching their username or steam ID. Another thing you can do is to social engineer them, but won't be explaining that any further.
Using Tools
- Dox Tool:
You can find it here. The program lets you do person search, email search, username search and it has a ip tracker and dox export. I personally only use the tool for it's username search. If you are trying to find information about a particular user, can be a HF user, Steam user or whatever and he or she has a unique name, then this tool can be very useful and save you time.
- IP logger:
First of all, when using any sort of IP logger you will want to hide the URL by using a URL shortener. Here are a few examples: You do not have permission to view the full content of this post. Log in or register now., You do not have permission to view the full content of this post. Log in or register now. and You do not have permission to view the full content of this post. Log in or register now.. IP loggers are pretty straight forward, you can use You do not have permission to view the full content of this post. Log in or register now. where you enter your email, and get your unique link that you will send to your target, but remember to hide it first using a URL shortener. Basically that will give you the IP of your target, this can be very useful if you do not have much to go on.
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.