Good day! Today, I'm going to show you how häçkers manipulate the files from the website that they häçked. häçkers used shell script to gain access from the web server and manipulate sensitive files. They can change your codes and can also add their own codes and delete some codes as well. Shell script is a computer program designed to be run by the Unix shell, a command-line interpreter. Typical operations performed by shell scripts include file manipulation, program execution, and printing text. So let's do this.
REQUIREMENTS:
Note: For tutorial purposes, I am going to use my own website.
STEPS:
1. Go to your website and then find a page where you can upload a file.
2. Download the shell script and extract it.
3. Once you extracted the file, upload the PHP shell script to your web.
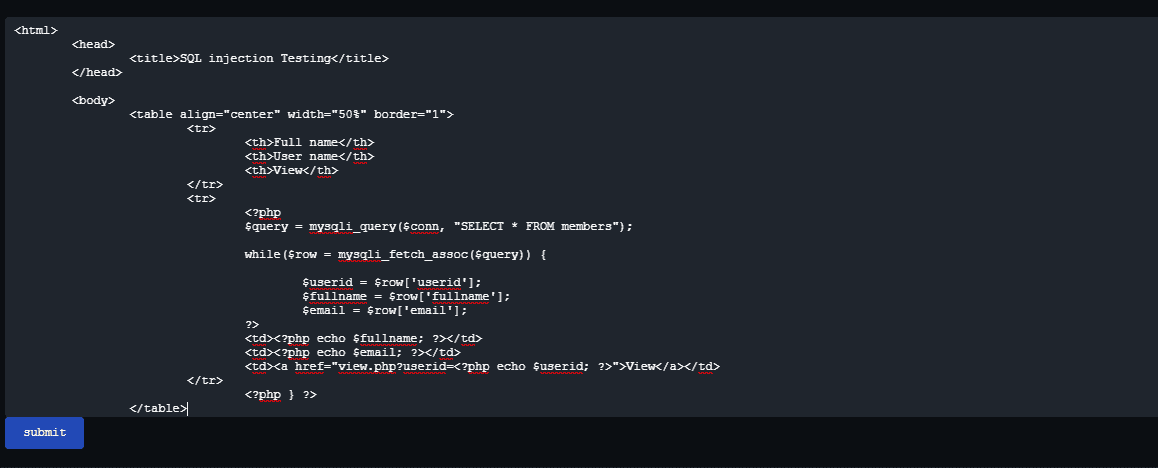
4. In my example, there is a link named View where I can view the file that I just uploaded. It is very very important to know the location of the uploaded file so that you can view your shell that you just uploaded. The shell that you just uploaded will act as a new page to your website. In my case, the uploaded files will be stored in uploads folder. So let's say that the name of our Shell script is wso.php which is stored in uploads directory. Therefor, to view the uploaded shell, we will go to:
Don't be confused. I am using a localhost since I build my project using Xampp. So now that we found the location where we can view our shell, you should see something like this:
NOTE: Your shell might be different when it comes to design. I am using a wso.php shell which is for PHP 7.
Notice that when you're inside your shell, you can view every files where in your website is stored. Clicking
 will redirect you to another directory page where you can view more files. You can also edit the codes of the .php files by clicking the file name.
will redirect you to another directory page where you can view more files. You can also edit the codes of the .php files by clicking the file name.
You can also delete the files and other data.
So, how can we prevent this kind of attack? First thing is... we need to learn on how to prevent our website in SQL injection vulnerabilities. Once you've done that, secure your upload function. The most basic thing to do to prevent häçkers in uploading shell script, we have to ensure that the uploaded file is actually the file that we want to store in our server. If you have an upload file functionality on your project where it will allow the users to upload some images or videos, you have to add a code where in it will check if the uploaded file is actually an image file or a video file. However, häçkers can now bypass this kind of filter using a Tamper Data. If you don't know what tamper data is, you can check it You do not have permission to view the full content of this post. Log in or register now..
To secure the upload function from tampering your data, you should first create a code that will fetch the file extension. There's a lot of ways to fetch the file extension in PHP programming.
example:
<?php
$array = explode('.', $_FILES['image']['name']);
$extension = end($array);
?>
or you can also do this:
<?php
$path = $_FILES['image']['name'];
$ext = pathinfo($path, PATHINFO_EXTENSION);
?>
once you've done that, you should create a code that will change the file extension to an acceptable extension that is required to your web site. There is also another way that will replace the file extension in PHP 7. for example:
function replace($uploaded_file, $new_extension) {
$info = pathinfo($uploaded_file);
return $info['filename'] . '.' . $new_extension;
}
Now that you have changed the file extension, you should also change the file name. there are a lot of ways as well to change the file name. some websites will encrypt the uploaded file before they're going to store it on their server. example:
$temp = explode(".", $_FILES["file"]["name"]);
$newfilename = round(microtime(true)) . '.' . end($temp);
move_uploaded_file($_FILES["file"]["tmp_name"], "../img/imageDirectory/" . $newfilename);
move_uploaded_file has 3 parameters and you can use the 3rd parameter to change the filename before it will be uploaded.
Hopefully you've learned something with this thread to secure your project. If you have some questions, you can message me or leave a comment.
REQUIREMENTS:
- website vulnerable in SQL injetion (Learn SQL injection here) you can use your web project as a test
- Shell script (you can download free Shell script
Note: For tutorial purposes, I am going to use my own website.
STEPS:
1. Go to your website and then find a page where you can upload a file.
2. Download the shell script and extract it.
3. Once you extracted the file, upload the PHP shell script to your web.
4. In my example, there is a link named View where I can view the file that I just uploaded. It is very very important to know the location of the uploaded file so that you can view your shell that you just uploaded. The shell that you just uploaded will act as a new page to your website. In my case, the uploaded files will be stored in uploads folder. So let's say that the name of our Shell script is wso.php which is stored in uploads directory. Therefor, to view the uploaded shell, we will go to:
Don't be confused. I am using a localhost since I build my project using Xampp. So now that we found the location where we can view our shell, you should see something like this:
NOTE: Your shell might be different when it comes to design. I am using a wso.php shell which is for PHP 7.
Notice that when you're inside your shell, you can view every files where in your website is stored. Clicking
You can also delete the files and other data.
So, how can we prevent this kind of attack? First thing is... we need to learn on how to prevent our website in SQL injection vulnerabilities. Once you've done that, secure your upload function. The most basic thing to do to prevent häçkers in uploading shell script, we have to ensure that the uploaded file is actually the file that we want to store in our server. If you have an upload file functionality on your project where it will allow the users to upload some images or videos, you have to add a code where in it will check if the uploaded file is actually an image file or a video file. However, häçkers can now bypass this kind of filter using a Tamper Data. If you don't know what tamper data is, you can check it You do not have permission to view the full content of this post. Log in or register now..
To secure the upload function from tampering your data, you should first create a code that will fetch the file extension. There's a lot of ways to fetch the file extension in PHP programming.
example:
<?php
$array = explode('.', $_FILES['image']['name']);
$extension = end($array);
?>
or you can also do this:
<?php
$path = $_FILES['image']['name'];
$ext = pathinfo($path, PATHINFO_EXTENSION);
?>
once you've done that, you should create a code that will change the file extension to an acceptable extension that is required to your web site. There is also another way that will replace the file extension in PHP 7. for example:
function replace($uploaded_file, $new_extension) {
$info = pathinfo($uploaded_file);
return $info['filename'] . '.' . $new_extension;
}
Now that you have changed the file extension, you should also change the file name. there are a lot of ways as well to change the file name. some websites will encrypt the uploaded file before they're going to store it on their server. example:
$temp = explode(".", $_FILES["file"]["name"]);
$newfilename = round(microtime(true)) . '.' . end($temp);
move_uploaded_file($_FILES["file"]["tmp_name"], "../img/imageDirectory/" . $newfilename);
move_uploaded_file has 3 parameters and you can use the 3rd parameter to change the filename before it will be uploaded.
Hopefully you've learned something with this thread to secure your project. If you have some questions, you can message me or leave a comment.
Attachments
-
You do not have permission to view the full content of this post. Log in or register now.